A personal data breach is a breach of security leading to personal data being compromised.
The GDPR governs how personal data should be protected from data breaches, and this article will explore the topic of data breaches in relation to the GDPR.
The severity of data breaches can vary significantly.
On the one hand, accidental data loss may occur without malicious intent and the involvement of malicious third parties.
On the other hand, deliberate attacks by hackers aiming to gain access to or misuse data present substantial risks. These targeted breaches elevate the probability of unauthorised disclosure, leading to significant harm to individuals and organisations.
The GDPR has a set of requirements which govern how companies must act when a personal data breach occurs.
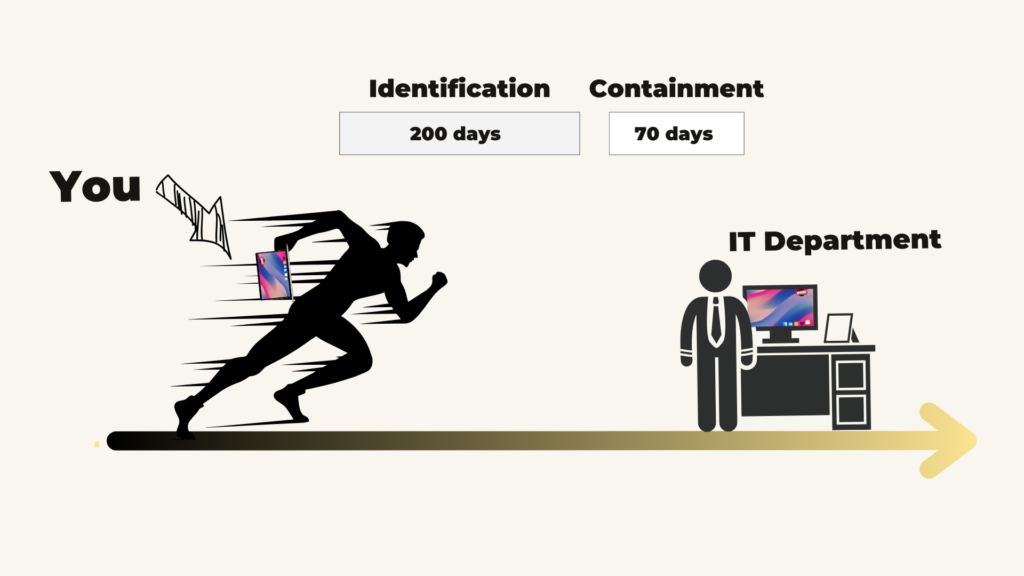
Interestingly, this also requires your company to have the capability to identify a data breach when it happens so that you can stop and mitigate it.
In the GDPR, ignorance is not an excuse for non-compliance. Your organisation must, therefore, be vigilant for data breaches and prepare the organisation to respond to a data breach.
How to Identify a Data Breach
It is important to be able to identify a data breach because this is the first to prevent and identify it when it happens.
What is a Personal Data Breach?
In the context of the GDPR, a breach in personal data security is defined as follows:
“A ‘personal data breach’ means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed”
Simultaneously, a breach in personal data security is also considered an information security incident. In the information security standard ISO 27000, an information security incident is described as a situation where there’s an identifiable occurrence involving a system, service, or network. This occurrence suggests a breach in the information security policy or a failure in the security measures. It could also be an instance that hasn’t been previously recognised but is potentially significant for security.
It’s important to note that only those information security incidents involving personal data fall under the definition of a personal data breach in the GDPR.
Therefore, not every information security incident is considered a personal data breach. For example, detecting unusual network traffic patterns could be classified as a security incident, but it doesn’t necessarily mean there has been unauthorised access to or disclosure of personal data.
This scenario shows the need for careful consideration to determine whether a genuine personal data breach has occurred, which is important for understanding and applying the GDPR rules effectively.
A Variety of Data Breaches
The purpose of the GDPR is to protect personal data, and avoiding personal data breaches is, therefore, one of the central concerns of the regulation.
You must, therefore, be aware of how personal data breaches might occur in practice so that you can implement appropriate measures to prevent and identify them if they happen.
A Data Breach Investigations Report by Verizon shows that 3 out of 4 data breaches include a human element with people involved through error, privilege misuse, stolen credentials or social engineering.
Data breaches can occur through various channels and often stem from inadequate safeguards in your organisation, which could be mitigated.
Types of Data Breaches
In the following, we will explore some of the main types of data breaches to give you an idea of how these data breaches occur.
Hacking
Hacking involves unauthorised access to data systems by exploiting technical vulnerabilities in your systems.
A hacker typically identifies weak points in a system’s security architecture, such as outdated software components, unsecured network connections, or poorly configured systems. Once the hackers find a vulnerability, they use various methods, such as injecting malicious code or using stolen credentials, to bypass security measures and infiltrate the system.
Accidental Disclosure
Accidental disclosure of personal data often stems from human error. Typical examples include mistakenly sending emails to incorrect recipients or database misconfigurations that leave private data accessible to the public.
Physical Theft or Loss
Data breaches can occur by losing or being robbed of devices like laptops, hard drives, or smartphones that store personal data. This highlights the need for physical security measures in addition to digital safeguards, such as encryption of hard drives in case a device gets stolen.
Insider Threats
Insider threats are a significant source of data breaches within organisations and roughly concern 20% of security incidents. They occur when employees or other insiders with legitimate access to information intentionally or accidentally cause a breach. This risk emphasises the importance of implementing internal security protocols.
Ransomware and Malware Attacks
Ransomware and malware attacks are types of breaches where malicious software is used to compromise your system’s security. Ransomware typically encrypts data, holding it hostage for a ransom, whereas other malware types might covertly extract information. These attacks highlight the need for anti-malware defences and regular system updates to ensure that malware can’t explore outdated software.
Causes of Data Breaches
The aforementioned types of data breaches would not happen without a combination of inadequate security measures, internal errors, and malicious external actors. In the following, we will explore some causes of data breaches.
Weak or Reused Passwords
Software users often create passwords they can remember and reuse across different accounts, leaving them vulnerable to being compromised. Simple or commonly used passwords are easily cracked, which offers an entry point for hackers to access systems.
Once hackers have compromised a reused password, several accounts will be vulnerable to access by hackers.
Phishing Attacks
A phishing attack is a deceptive technique where a cybercriminal impersonates someone else to have the victim perform an act, e.g., reveal sensitive information. A phishing attack is often performed by sending emails imitating a trusted person and luring the recipient into clicking a malicious link or providing personal details.
CEO fraud is an example of a phishing attack where hackers establish a false identity of a trusted figure as the CEO, which would then ask the victim, often an employee, to transfer money, make a purchase on their behalf, or reveal secret information.
The infamous “Nigerian Prince” scam is another example of a phishing attack. Here, the “Nigerian Prince” requests help to transfer a large sum of money and will falsely reward you(the victim) with a small fee.
Software Vulnerabilities
Software is developing rapidly, and the software you use every day continuously adds new features, performance updates, etc., to ensure it runs smoothly and integrates well with the systems it depends on.
Your company uses a lot of software, requiring significant work to ensure it all works together while maintaining the software updates.
This often leads to software with outdated or unpatched software, which is prone to breaches as attackers can exploit these weaknesses.
Human Error
Human error is the cause of 1 out of 10 data breaches, according to Verizon’s Data Breach Investigations Report.
Employees are exposed to significant technological changes and are expected to do more in less time in high-paced work environments. Therefore, mistakes such as sending data to incorrect recipients or mishandling information happen daily in organisations.
This is why employee awareness training in data protection, cybersecurity, and compliance is a commonly used organisational measure to increase security.
Inadequate Security Measures
A lack of comprehensive security infrastructure, including poor network security, insufficient employee training, and weak access controls, increases vulnerability to various threats.
Both small and large companies have difficulties with implementing appropriate security measures. As already mentioned, the speed of development, the scale of data processing, organisational complexities, the rate of change, and a lack of information security talent, budgets, and awareness about the issue cause organisations to have inadequate security measures.
Small companies often need to gain know-how about security and find the implementation and maintenance costly. For large companies, the organisation’s size can make it complicated to ensure safety in all corners.
Examples of Personal Data Breaches
In the previous sections, we explored the types of data breaches and some of the causes that would allow such data breaches to happen.
In order to provide a clearer understanding of the concept of a personal data breach as defined by the GDPR, the following examples can be used as illustrations:
- An unauthorised person, whether outside or inside the company, access personal data they shouldn’t have access to.
- An employee accidentally changes or deletes personal information, leading to unintended data loss.
- Someone gains insight into personal data, like social security numbers or credit card information, due to a server breach at the company.
- An employee shares private information about a customer with someone else, either by mistake or on purpose, leading to unauthorised disclosure.
- The loss or theft of devices like laptops or smartphones that hold unencrypted personal data allows unauthorised access to personal data stored on the devices.
- Personal data is mistakenly sent to the wrong person via email or traditional mail.
- A cyberattack, such as phishing or malware, steals personal data from the company’s systems.
- Personal data is accidentally exposed on a public website due to coding errors or misconfiguration.
- An employee views personal data without a valid business reason, breaching internal data access policies.
- Personal data is disposed of insecurely, such as paper records not being shredded appropriately, whereby somebody can find personal data in the dumpster outside the building.
These examples are simply some of the endless ways personal data could be compromised and lead to a data breach.
Impact of Data Breaches on Individuals
The repercussions of a data breach can significantly impact the affected individuals, ranging from minor inconveniences to severe, life-altering situations. The nature of the data breach, the categories of personal data compromised, and the individuals affected all play a role in determining the severity of the consequences.
The following examples illustrate some of the negative outcomes of a data breach:
Incorrect Medical Treatment
A breach in health data could lead to wrong medical treatment if critical information like allergies or medication details is altered, potentially causing severe health complications.
Financial Fraud
An exposure of personal financial data can lead to financial fraud, where victims may lose money through unauthorised transactions or identity theft.
Loss of Employment
If confidential employment records are exposed or tampered with, it could lead to missed career opportunities, wrongful termination, and significantly impact an individual’s livelihood.
Identity Theft
A common and severe consequence of personal data breaches is identity theft, where the victim’s identity is used for illegal activities, which could lead to legal complications for the individual or similar troubles.
Blackmail and Extortion
Exposure of personal information can lead to blackmail and extortion, especially if the data includes compromising photos, messages, or information that the individual wishes to keep private.
Legal Consequences
Sometimes, people find themselves in a situation where they need to go through legal battles to clear their name or fix fraudulent activities that were done using their identity. Unfortunately, this can end up costing them a lot of money in legal fees.
Reputation Damage
Disclosure of sensitive personal information, such as sexual preferences, can lead to social stigma, damaging an individual’s personal and professional reputation.
Future Security Risks
Stolen data can be used for ongoing criminal purposes, which puts people at greater risk of cybercrime and personal security risks.
GDPR and Personal Data Breaches
The GDPR sets out specific requirements and procedures for handling data breaches.
Your organisation is obviously incentivised to respond to personal data breaches promptly to mitigate the damages, but the GDPR also regulates how your organisation should respond.
The following will examine how to stay GDPR compliant when handling a data breach.
GDPR Requirements in a Data Breach
When a data breach has been identified, you must take immediate action to contain the breach and to ensure GDPR compliance, including clear communication with stakeholders, notification to affected individuals, and maintaining thorough internal documentation.
The GDPR is a framework that you must follow. Furthermore, it also assists you in ensuring that you handle data breaches in a way that serves all stakeholders affected by the breach.
These requirements for handling a personal data breach are explained in the following sections.
Notification to the Authorities
When you identify a data breach in your organisation, you must notify the supervisory authority immediately. The deadline for making this notification is within 72 hours of becoming aware of a data breach.
If your notification is delayed more than 72 hours, you must include an explanation of the reasons for the delay to the supervisory authority.
When the data breach is unlikely to result in a risk to any individuals, you are not obliged to notify the data protection authority.
You can learn how to evaluate a breach further in this article, which will also specify when you are not obliged to notify the data protection authority.
The Content of the Notification
The notification to the supervisory authority must describe the facts of the personal data breach, such as what caused the breach. It must include the categories of data subjects and the approximate number of data subjects affected by the breach, the types of personal data included, e.g., email address, username, etc, and the number of these.
You must include the contact details of your organisation’s contact person, which would be the data protection officer if you have appointed one.
The notification must describe the likely consequences to the affected individuals and the measures taken or proposed to address the personal data breach and mitigate the consequences for the individuals.
If you cannot report the full details within 72 hours, then you can provide the information in phases to respect the 72-hour deadline.
No matter what, you must always document all personal data breaches in your internal records according to the abovementioned requirements. The data protection authorities can always request this information to verify you have complied with these rules.
Notification of the Affected Individuals
When the data breach is likely to result in a high risk to the affected individuals, you must notify them immediately so that they can protect themselves, e.g., by changing passwords to breached accounts.
The notification should be clear and transparent about the facts of the data breach and at least include the details of the contact person, e.g. the data protection officer or similar, the likely consequences of the data breach, and the measures your organisation is taking to mitigate the negative consequences to these individuals.
The notification should be made directly to the affected individuals to ensure they receive the information unless this is a disproportionate effort. If it is impossible to ensure that everyone gets the information directly, indirect measures could be used, like issuing a public statement, e.g. via a press release.
Data Processors and Data Breaches
Most organisations use vendors, including data processors.
When a data processor identifies a data breach affecting the data processed on behalf of the data controller, it must notify the data controller immediately. This will enable the data controller (your organisation) to follow its obligations to report the data breach to data protection authorities and the affected individuals.
Assessing a Data Breach
The expected impact of a data breach is important to determine to manage the data breach effectively. The following will explore how a data breach could impact individuals.
Type of Breach
The nature of a data breach will influence its repercussions on the affected individuals. The theft of an encrypted hard drive resulting in the loss of a person’s social security number differs from when a misconfiguration publicly discloses the social security number.
The Sensitivity of Personal Data
The sensitivity of the personal data involved influences the risk assessment. For example, an accidental public disclosure of information about someone’s criminal history, debt, or health condition could have more far-reaching implications than the exposure of their email address or phone number.
Risk of Identification
Personal data might have been involved in a data breach, but you should consider how easily affected individuals can be identified from the compromised data. If the compromised personal data is on an encrypted hard drive, it reduces the identification risk.
Consequences
The severity of a breach depends on the group of individuals affected by the breach. For instance, breaches involving particularly vulnerable people, such as children, could be more damaging.
Information in Criminal Hands
If it is known that the compromised data has reached criminals with malicious intent, this significantly influences the risk assessment of the data breach. This would be the case with a ransomware attack.
Recipient’s Trustworthiness
Suppose you have sent personal data to the wrong person, but you expect the recipient to follow instructions to return or destroy the data. In that case, the breach might be viewed as having no significant consequences. However, the data controller should be confident about the recipient’s reliability and, if possible, have documentation confirming the data is no longer accessible to them.
Reversibility
Breaches with long-lasting or permanent effects are considered more serious. These would be breaches the data controller, or the individual can’t easily remedy. For example, leaked payment card details can be mitigated by cancelling the card, but leaked information damaging someone’s reputation can have longer-term impacts.
Size Matters
Generally, the larger the number of individuals affected by a breach, the more significant the impact. However, breaches involving just one or a few individuals can also have serious consequences when the data is sensitive.
Characteristics of the Data Controller
The affected organisation’s characteristics and processing activities can affect the likelihood that a breach poses a risk to individuals. For example, a private hospital handling extensive health information or a credit bureau processing data on bad debtors heightens the risk to individuals.
Considering the abovementioned aspects can help evaluate the potential impact of a personal data security breach and guide you to the appropriate response measures to protect the individuals affected.
How to Respond to a Data Breach
In all emergencies, immediate actions should be taken to contain the incident and its damages.
Immediate Actions
The initial response to a data breach requires decisive action to contain it and assess its scope. This may include isolating compromised systems, revoking access privileges, and securing physical areas if necessary.
A preliminary assessment of the data breach should determine the type and extent of data compromised and whether the breach is still ongoing.
You should already have a data breach plan, which also includes the response team members. If you haven’t done so already, assembling a response team comprising members from IT, legal, and communications departments and upper management is useful to manage the breach effectively. This team is also responsible for documenting every step taken to mitigate the breach, which will be used for regulatory compliance and any legal proceedings.
Communicating with Stakeholders
In the chaos of a data breach, clear and transparent communication is key in managing it in an organised manner.
Internally, your colleagues should be informed about the breach and understand their roles in responding to the data breach.
Externally, you must communicate to the affected individuals as soon as possible (if there is a risk of negative consequences) and follow the GDPR requirements in Article 34.
You should also engage with the data protection authorities and be transparent and cooperative, providing all necessary information about the breach and the response actions while following the requirements of Article 33.
Role of Data Protection Officers (DPO)
When an organisation appoints a Data Protection Officer, this person has several critical roles concerning a data breach.
During a personal data breach, the DPO advises the response team to comply with the GDPR. This includes ensuring that the data breach notifications sent to the data protection authority and affected individuals align with GDPR requirements. The DPO can assist in categorising the data involved in the breach, evaluating the potential risks to individuals, and assessing the suitability of proposed or implemented measures to address the breach.
The DPO can also play a role in internal communication and coordination with IT, legal, and communications departments to ensure a compliant response strategy and that all actions are documented accurately.
After a breach has been managed safely, the DPO should collaborate with relevant internal stakeholders to analyse the incident, identify lessons learned, and suggest improvements to prevent future breaches.
Notifications
When to Notify Individuals
As noted earlier, the GDPR require you to notify the data subjects when it is likely that the breach poses a high risk to the rights and freedoms of these people.
This notification should be clear and concise, explaining the nature of the breach, the categories of data involved, the potential consequences, and the steps taken to address the breach.
The goal of the notification is to ensure that the affected individuals can take appropriate steps to protect themselves from potential harm.
Notifying individuals primarily enables them to take necessary precautions if their data has been compromised. As highlighted earlier, a breach in personal data security can lead to significant adverse effects on those impacted – such as discrimination, identity theft or fraud, financial loss, reputational damage, loss of confidentiality of data protected by secrecy, or any other economic or social disadvantage.
The concept of “high risk” in data protection regulations is not explicitly defined. Nevertheless, according to the risk assessment guidelines, the severity of potential consequences and the likelihood of a data breach’s implications for individuals contribute to a higher level of risk.
When conducting a risk assessment, the data controller should consider all potential outcomes and negative effects on individuals. This includes “secondary” consequences that could occur due to a breach in personal data security.
Furthermore, notification should be provided regardless of the number of individuals affected, based on the potential severity of the adverse effects. This approach ensures that all potential impacts on individuals’ rights and freedoms are adequately addressed.
When Not to Notify Individuals
A Data Breach Does Not Pose a High Risk
Notifying the affected individuals is not necessary in cases where a data breach is assessed as not likely to pose a high risk to the rights and freedoms of individuals.
The burden of proof to demonstrate that there is no high risk lies with the data controller. They must be able to justify, if required, for instance during an inquiry by the Data Protection Authority, why they chose not to notify the individuals affected.
Appropriate Technical and Organisational Measures
If the data controller, after assessing all potential consequences and negative impacts of a data breach, concludes that the breach is likely to involve a high risk to individuals’ rights and freedoms, the default action is to notify the individuals affected.
However, notification is not required if the data controller has implemented appropriate technical and organizational protective measures, such as encryption, which make the personal data unintelligible to unauthorized individuals.
For example, if a data controller loses a portable device containing encrypted personal data, and the encryption used is strong enough that it cannot be broken or bypassed for a significant period, and there’s no likelihood of unauthorized decryption – such as by obtaining the encryption key – then it can be assumed that the personal data is protected to an extent that the breach likely does not pose a high risk to individuals’ rights and freedoms. The data controller carries the burden of proof to justify their decision not to notify the individuals affected.
In cases where a data breach is assessed to have a high risk of negatively impacting individuals’ rights and freedoms, the default action is to notify affected individuals. However, notification may not be required if appropriate technical and organisational measures, such as encryption, are in place to make the personal data unintelligible to unauthorised individuals.
For instance, it can be assumed that personal data is protected if a data controller loses a portable device containing encrypted personal data, the encryption is sufficiently robust, and there is no likelihood of unauthorised decryption (such as obtaining the encryption key).
The data controller would still be responsible for justifying the decision not to notify the affected individuals.
Unexploited Risks
Suppose a data breach occurred, but it was stopped before the data breach could be exploited. In that case, notification of the individuals is not necessary.
For example, suppose an IT system accidentally creates unauthorised internet access to personal data, but it gets discovered immediately, and access is blocked. An internal investigation of logs could confirm whether only authorised users accessed the data during the exposure, which would determine whether or not individuals were affected and should be notified.
Disproportionate Effort
In some cases, the data controller may choose not to notify each individual directly if the effort required to do so is considered disproportionate to the circumstances.
The decision to notify individuals about a data breach must balance the importance of informing them against the effort required.
For example, a company that loses access to all customer data as a result of a ransomware attack on its customer database might fall under this exception. In such a scenario, if an internal evaluation determines that individual notification would require an excessive amount of effort, the data controller should consider alternative measures, such as a public announcements to inform the affected individuals.
Responsibility and Internal Documentation
Organisations are required by the GDPR to keep a record of all data breaches, regardless of their size and severity.
The internal record of data breaches should include the facts of the breach, its effects, and the remedial actions taken.
This documentation also serves as a critical tool for refining future data protection strategies and responses, because it helps organisations to analyze patterns, identify weaknesses in their data protection strategies, and implement more effective measures instead.
Legal Consequences of a Data Breach
Personal data breaches can lead to significant legal consequences, including fines and penalties. In the worst-case scenario, an organisation can be fined 20 million euros or 4% of the annual revenue, whichever is higher, and even be sentenced to prison.
In the eyes of the regulation, any data breach is punishable, so you can both be the victim of getting hacked and get fined by the supervisory authority for negligence at the same time.
This might seem unfair at first glance, but GDPR compliance requires organisations to implement appropriate technical and organisational measures to mitigate the risk of potential negative consequences for the data subjects. If it is found that such measures were not effectively in place when the breach took place, then your organisation risks getting fined.
Determining a fine depends on several factors, including the nature, gravity, and duration of the infringement, the intentional or negligent character of the violation, and actions to mitigate the damage.
Case Study: Marriot International Data Breach
Hackers accessed the reservation systems of Marriott’s Starwood properties, affecting up to 339 million guests in 2018. The Data Protection Authority of the UK (ICO) initially announced a fine of £99 million, which was finally reduced to £18.4 million. The breach underscored the need for due diligence in IT security during mergers and acquisitions.
The UK’s Data Protection Authority issued the fine to Marriot International and identified four failures by Mariott International, which were the reasons behind their fine.
1. Insufficient Monitoring of Privileged Accounts
The intruder managed to access the Cardholder Data Environment of Marriot (CDE) by taking advantage of a previously unidentified weakness in applying Multi-Factor Authentication, which was not applied to all accounts and systems with access to the CDE.
Their failure in this regard was that they could have been more effective in monitoring user activities, especially those with high-level access.
This lack of detailed surveillance and logging within their systems made it difficult to detect anomalies, such as unauthorised actions within the CDE. This oversight in monitoring and logging made them unable to identify unusual account activities and potential breaches.
2. Insufficient Monitoring of Databases
Insufficient monitoring of databases within the CDE was a key failure in Marriott’s data protection, as identified by the data protection authority. There were three primary reasons for this:
Marriott’s configuration of security alerts on its databases was inadequate. This flaw meant the system failed to effectively signal suspicious activities within the CDE, which would have been critical in identifying potential breaches.
Secondly, Marriott should have properly aggregated logs from different sources. Aggregating logs is essential for comprehensive analysis of network activity, allowing for a more holistic view of potential security threats.
Thirdly, Marriott’s logging of activities within the CDE was insufficient, particularly in recording actions like file creation and exporting database tables – this lack of detailed logging limited its ability to detect unusual or unauthorised activities across its systems.
These three shortcomings in database monitoring contributed to Marriott’s delayed detection and response to the data breach.
3. Control of Critical Systems
Marriott’s control of critical systems was considered inadequate by the data protection authority because of poor monitoring and insufficient server hardening.
They hadn’t implemented effective whitelisting, which would have restricted system access to authorised users or IP addresses.
Marriott’s implementation of whitelisting was limited and argued it was burdensome on IT systems. However, whitelisting had been a well-established practice even before the GDPR era.
Additionally, Marriott’s security approach lacked a comprehensive ‘defence in depth’ strategy with layered protection and monitoring of network activities.
4. Lack of Encryption
Marriott focused mainly on PCI DSS compliance (Payment Card Industry Data Security Standard) and argued that this was a risk-based approach, targeting security efforts on database tables containing cardholder information. However, this approach led to inconsistencies, such as encrypting some but not all passport numbers or other personal data categories, which also need protection.
The existence of efficient decryption methods such as unique identifiers and Hardware Security Modules contradicted Marriott’s assertion that extensive encryption was impractical. Furthermore, a vulnerability within their guest reservation database compromised the security offered by encryption, enabling the decryption of encrypted entries. This incident highlighted the shortcomings of Marriott’s approach to safeguarding personal data.
Summary
Altogether, the case study of the Marriot International data breach illustrates that you must have a thorough approach to the security of personal data to comply with the GDPR.
In this case, the intruder accessed Marriot’s systems before the GDPR went into force, but as they failed to discover the breach promptly, they were still considered non-compliant with the GDPR.
The Cost of Data Breaches
Beyond the immediate harm to individuals whose data is compromised, data breaches come with a cost for the businesses experiencing the data breach.
The average data breach costs a company more than 4 million euros, according to IBM’s report “Cost of a Data Breach Report”. However, the cost of a data breach can vary substantially, depending on factors such as the country where the breach occurs, the size of the affected company, the industry it belongs to, the timeliness of the incident response, and the overall maturity of the company’s IT security measures.
The Data Controller’s Cost
The aftermath of a breach necessitates investigations, containment efforts, system restoration, and often the hiring of external cybersecurity specialists. These expenses add up rapidly.
An organisation will be at risk of being fined if negligence is the cause of the data breach. Data protection regulations, like the GDPR, impose significant penalties for non-compliance of up to 4% of an organisation’s global revenue or 20 million euros.
Individuals impacted by a data breach may be entitled to compensation if they experience financial losses or damage to their reputation, which might also lead to costly legal disputes if these are contested.
Data breaches often impact business operations and cause downtime and lost productivity. Sometimes, it can negatively affect sales if it affects sales processes, delivery times or similar.
Perhaps the most insidious cost is the erosion of trust. A data breach can tarnish a brand’s reputation, deterring current and potential customers. This loss of trust can linger and impact the company’s bottom line for years.
The total cost of a data breach varies depending on the scale and severity, but even minor breaches can prove financially devastating. Proactive measures like robust cybersecurity protocols, employee security awareness training, and incident response planning are basic investments that mitigate the potential costs of data breaches.
Summary
In this article, you have learned what a personal data breach is in relation to the GDPR, how to identify a data breach in practice, how to assess a breach, and how to respond in a GDPR-compliant manner. We have also explored cases of data breaches and the costs to your organization from a data breach.